Introduction
Frida is a portable dynamic instrumentation Framework.
With Frida you can get your own JavaScript code injected into any process, hook any function, trace code. It works on Windows, Mac, Linux, iOS and Android.
Frida's core is written in C and injects Google's V8 engine into the target processes.
In this tutorial you will learn how to install Frida and how to hook a function in Mozilla Firefox.
Installation
Frida should only take only a few minutes to get installed on your system.
Requirements
Install with pip
We recommend you to install Frida via PyPI if you have successfully installed setuptools just run the following command.pip install frida
Firefox PR_Write hooking
We want to spy on the content a user is browisng in Firefox.
According to the Mozilla Developer Network PR_Write is the function responsible to write a buffer of data to a file or socket.
The function has the three following parameters:
fdA pointer to the PRFileDesc object for a file or socket.bufA pointer to the buffer holding the data to be written.amountThe amount of data, in bytes, to be written from the buffer.
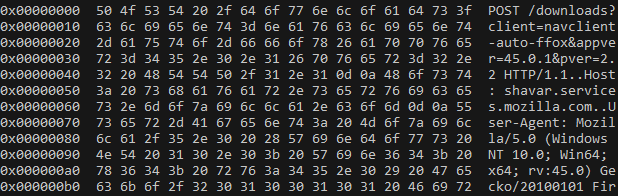
The Python code below is able to to grab the content pointed by buf from all requests.
import frida
import sys
session = frida.attach("firefox.exe")
script = session.create_script("""
"use strict";
const PR_Write = Module.findExportByName("nss3.dll", "PR_Write");
Interceptor.attach(PR_Write, {
onEnter: function (args) {
let length = args[2].toInt32();
let buffer = Memory.readByteArray(args[1], length - 1);
console.log(buffer);
}
});
""")
script.load()
sys.stdin.read()Conclusion
With the 15 lines of code above you should be able to read and modify all requests made by Firefox without caring if it's a 32-bit or 64-bit process.
Note
Somehow the POST requests are not in cleartext it might be a protection mechanism.