Introduction
An Israeli security researcher named Danor Cohen recently discovered a WinRAR file extension spoofing vulnerability.
It allows attacker to modify the name and the extension of any file inside an archive.
Danor Cohen noticed that WinRAR adds some custom properties to an archive, including two names.
The first name is the original filename and second name is the filename that will appear at the WinRAR GUI window.
WinRAR structure
I created a basic ZIP archive file using WinRAR, the original file name is wiremask.txt.
With the help of a Hexadecimal editor the attacker can manipulate the second filename and extension to craft a special ZIP archive, that can actually include a malware file wiremask.exe, but displaying itself as wiremask.txt to the WinRAR user.
Demonstration

For the demonstration I modified the .txt extension of the second file name in the wiremask.zip file with a .jpg. The result will be a WinRAR file that shows you an image file named wiremask.jpg, but when you double click it, the wiremask.txt file opens.
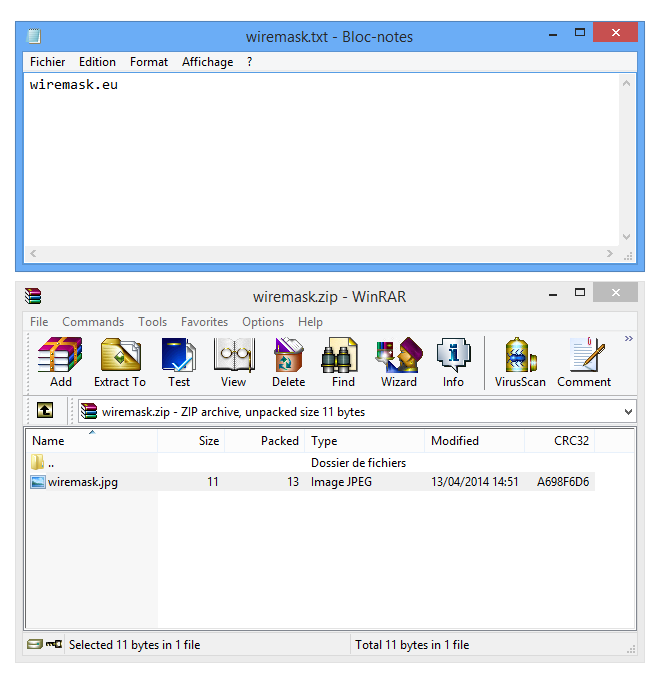
To success the user must double click the spoofed file. If the user extracts the file "Extract Here" from the archive, they will see a file that named wiremask.jpg turning into wiremask.exe which is very suspicious, then the exploitation might fail.
An attacker can add a password to the archive to prevent Virus Scanner to read the data inside the archive.
This vulnerability was successfully exploited in WinRar version 4.* and 5.* but it should be fixed in the next releases.