Introduction
In this article we will summarize the different methods that were used to complete the four forensic challenges during the HackingWeek 2015.
We recommend to use a Linux distribution and install a memory forensic framework such as Volatility or Rekall.
L'image mémoire fournie a été capturée sur une machine compromise à vous de l'analyser pour répondre aux questions (il s'agit de la même image pour les quatre épreuves de forensic, inutile de la télécharger plusieurs fois).
First we extract the memory sample with gunzip dump.gz. Then we get informations about the sample with the command vol.py -f dump imageinfo.
Forensic 1
Pour obtenir la clef de validation de cette épreuve est donnée par le PID, le PPID et le nombre de threads du programme
Solitaire. Mettez-le au format suivantPID:PPID:nThreads.
We need to find 3 numbers, the Process ID of Solitaire.exe, its Parent Process ID and its number of Threads.
$ vol.py -f dump --profile=Win7SP0x86 pslist
Offset(V) Name PID PPID Thds
---------- -------------------- ------ ------ ------
0x84729030 Solitaire.exe 2992 1312 8Forensic 2
L'un des utilisateurs de la machine venait de consulter plusieurs sites Web à propos d'un incident qui impliquait une personnalité de showbiz. La clef de validation est le
PrenomNomde cette personnalité.
We need to find the name of a celebrity in the memory dump. I tried to grep my own first name and last name but it couldn't find anything.
After some grep and multiple keywords we found several occurrences of Harrison Ford.
$ strings dump | grep http | less
$ strings dump | grep harrison | lessForensic 3
Trouvez le mot de passe de l'utilisateur admin qui se trouve quelque part en mémoire.
We have to find the password of the user "admin", after dumping the passwords we can find the hash.
$ vol.py -f dump --profile=Win7SP0x86 cachedump
p.dumont:b2992223764dde5403684a2da3620774:underground:underground.fr
admin:1bbeb11362554add15eba84d545f38f5:underground:underground.fr
c.prevost:1251fe313fec6bc0d878625a4bca2168:underground:underground.fr
j.navarro:8902907b5dedcae211adecaf9192183b:underground:underground.fr
f.lefevre:3c953d0c2c700fd09c4fc98381ea8409:underground:underground.frUnfortunately we were unable to crack the hash so we had to find another way around.$ strings dump | grep --color=always -B4 -A20 "mimikatz" | less -R
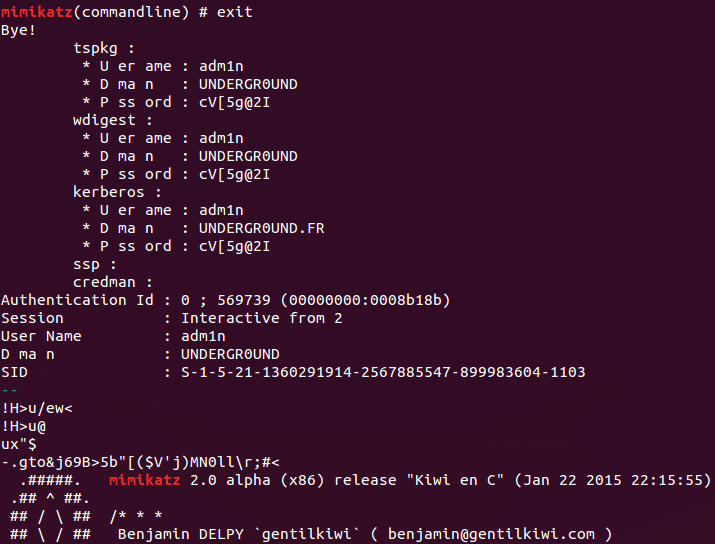
Finally after some more guessing we found a corrupted mimikatz dump containing the plaintext password.
Forensic 4
Lors de la compromission de la machine, l'attaquant a installé un logiciel de Command & Control qui est inactif pour le moment mais qui doit contacter un serveur pour recevoir ses ordres. Trouvez le nom du serveur et le port sur lequel le malware doit se connecter. La clef de validation sera
servername:portnumber.
For the last challenge we have to find the suspicious process, dump it to a file and do some reverse engineering to find the hostname and the port used by the Command & Control server.
Finding a suspicious process
We can see that there is something wrong in the process tree below, how could iexplore.exe have notepad.exe as a parent. We are going to dump the process with the id 3468 into a file and analyze it.
$ vol.py -f dump --profile=Win7SP0x86 pstree
Name Pid PPid
-------------------------------------- ------ ------
. 0x84033030:iexplore.exe 1088 1312
.. 0x841dba88:iexplore.exe 2456 1088
.. 0x84126340:iexplore.exe 3916 1088
... 0x83e4ed40:notepad.exe 4088 3916
.... 0x83e6dac8:iexplore.exe 3468 4088
$ vol.py -f dump --profile=Win7SP0x86 procdump -D dump/ -p 3468Finding the hostname and port
After opening the process with your favourites disassembler you can realize it's not internet explorer but definitely a malware.
The hostname is obfuscated but after some debugging you can grab it in the memory.